Let’s talk Citrix Virtual Applications. To do that, we first need to explain what a Citrix Virtual Application is. These applications are hosted on a Citrix Server that utilizes the Microsoft Remote Desktop Service (RDS) to publish virtual environments. Ideally, the applications are isolated from the underlying operating system, and are delivered to the user through the use of a Citrix Receiver that the user needs to install on their machine.
Many large applications use this infrastructure so testing these kinds of apps offers a different set of challenges to a penetration tester than those experienced when just testing normal web applications. What’s all that mean? Testing these = much more fun for those of us that like to learn new techniques and think outside the box.
Today’s tale begins with one of our Ninjas testing one such Citrix Application. One of the goals when testing a Citrix environment to “break out” of the environment and access the underlying system then continuing your adventure from there. As I said above, “ideally, these applications are separated from the underlying operating system” but this is not always the case and we’re here to find out when they’re not. So the lesson of today’s story is how the Ninjas escaped the Citrix environment, bypassing the controls, and going on to explore the rest of the castle… Er environment.
The first thing Ninjas noticed in this application is that there are several boxes that allow a user to enter hyperlinks. Using this, we can add a hyperlink that points to a file on the Windows file system. Since windows has default applications that it calls when opening certain file types, when we call a common file on the system say the system.ini file located “C:\Windows\system.ini”, the default application will be launched to open this file. In this case, the link opens notepad++. Well hello there, opportunity. First thought, “Awesome. Notepad++ has so much functionality.”

So the mighty Ninjas wielded their trusty notepad++ skills and used that functionality to advance their engagement, breaking out of their Citrix prison. Ideally, the plan would be to open an instance of powershell or cmd.exe. Sadly, after attempting to summon (calling) these applications using the above method, we received messages that they had been disabled on the system. Bummer. This is a great example of a vendor adding additional controls in an attempt to prevent what we are trying to do… Ninjas don’t quit so we continued onward.
After attempting several functions in notepad++, we settled on the run function. Our initial efforts were met with repeated failure as the applications had been disabled on the system, meaning we couldn’t bypass using those controls… So a bit more trial and error, revealed that…

leaving the window blank would open an explorer window. Cha-ching.

So current challenge- all access to C: for browsing has been disabled. Ninjas can see a mounted E:, but none of the files or anything of interest is there so how can we get to C:? Aha. Solution identified. We’re gonna utilize shortcuts.
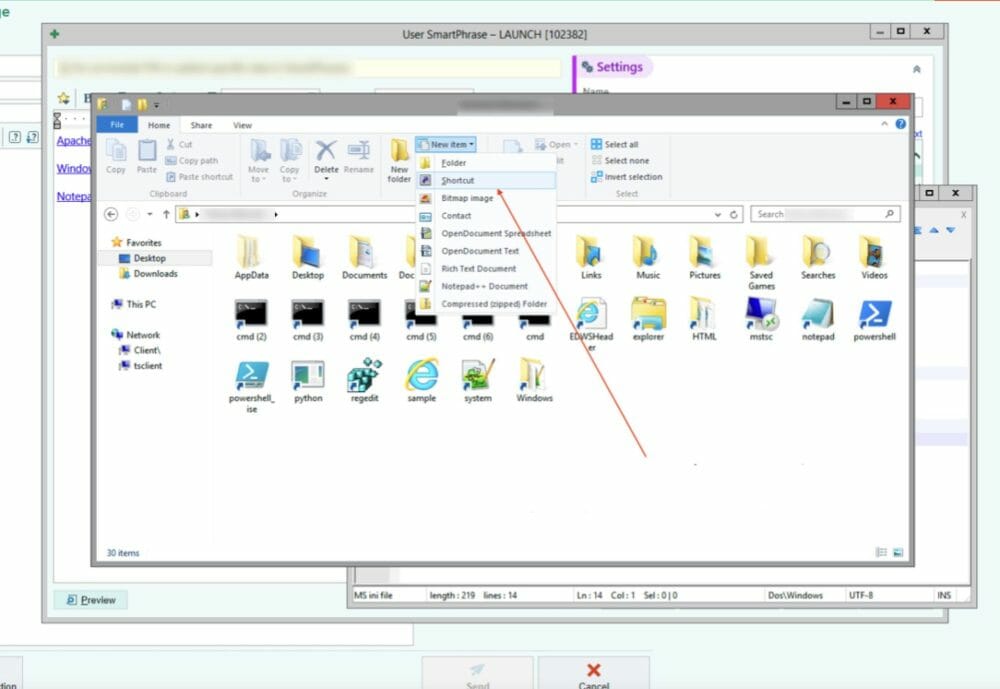
Some fun shortcut functionality is the ability to run a command. You can utilize the /k option to run something like “cmd.exe /k whoami”.

Success! We can now run commands, but because the cmd prompt is disabled, we still do not have an interactive shell. Ninjas kept pressing forward. After trying to run everything under the sun, someone suggested an interesting work around.

What if we run the shortcut as another user?

Bazinga! The command runs and the ninjas now have an interactive shell. Objective accomplished!
So the Ninjas utilized their handy dandy toolkit and escaped the might Citrix castle. I hope this was an interesting read for you. I know we had fun getting to this one. Remember, when performing an assessment if you hit what appears to be a wall, take a step back and try coming at the problem from another angle. Until next time.



